| Previous | Next |
| NTE_NOT_FOUND | NTE_BAD_PROVIDER |
NTE_DOUBLE_ENCRYPT
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. Windows crypt system can return NTE_DOUBLE_ENCRYPT (0x80090012) if the application attempted to decrypt the same data twice. he CryptDecrypt function decrypts data previously encrypted by using the CryptEncrypt function.
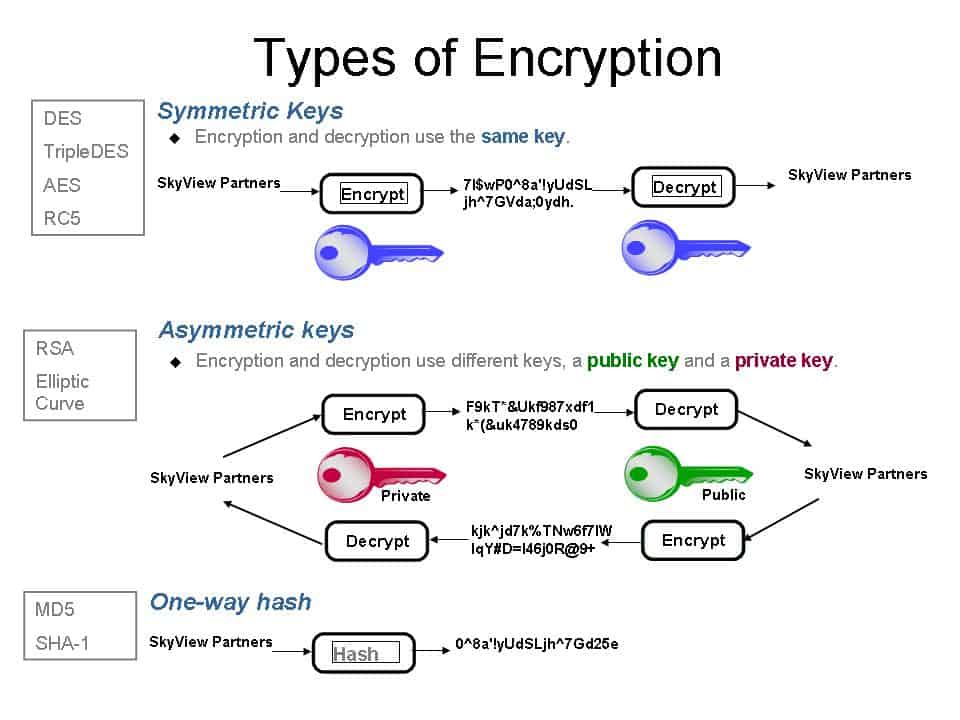
For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users.
Is it possible to encrypt encrypted data? NTE_DOUBLE_ENCRYPT?
Yes, in fact, chances are there are multiple layers of encryption on the socket you’re using to view this web page of What Is service.
A lot of different file/disk encryption programs even ask if you’d like to encrypt your data using multiple algorithms (e.g. using AES-256 followed by Blowfish, or some other algorithm).
When you encrypt something using multiple layers of encryption, it’s not that you need different programs to decrypt, just that the program you’re using to decrypt can properly decrypt the algorithm used at each layer, and more importantly that you select the correct order of algorithms when decrypting.
I was also wondering if encrypting it again would make it almost uncrackable, or if it would be the same as normal encryption
To this; no encryption is completely “uncrackable”. Even AES has a known vector of attack, but more specifically, it’s about entropy, or how long it will take to brute force the password, and knowledge of the algorithm used.
If I know that a file was encrypted using one of the DES algorithms, I could probably throw together a small beowulf cluster and brute force the password relatively shortly (within a few weeks or less). If I were to receive the same file but had no clue what algorithm was used (DES/AES/Blowfish/etc.), then more investigation would have to occur before I could attempt to crack it properly (or I could throw it to the various “crackers” while I’m investigating, knowing that it might be a waste of computational time).
Certain algorithms are known to have attack vectors that shorten the brute force time (like collisions, etc.), and thus are less secure than others, so knowledge of what container/algorithm was used shortens the time to brute force the encryption.
With that, if you were to encrypt a file with different algorithms, this just increases the time it would take to brute force the file. Mind you, if you use weak encryption for all levels, “time” is a relative term.
In the end, it just like picking a lock:
- How much time am I willing to invest in picking the lock?
- Is what’s behind the door that valuable as to warrant me spending that time on picking the lock?
- Is what’s behind the door that valuable as to risk being caught during the time it takes to pick the lock?
If someone else has something of value behind a less secure door, chances are I’ll go for that door over yours.